Risk controls
Adjust how aggressively you block fraud for your business with Radar for Fraud Teams.
Settings
To adjust the default risk score for blocking payments, use Radar for fraud teams. Go to the Radar risk controls page to make your adjustments.

The risk settings dialog shows your block threshold, your dispute rate, and other important statistics
Note
Adjusting the risk score applies to card, ACH, and SEPA Direct Debit payments. To test the outcome a different threshold might have on payments from a specific payment method, select a payment method and test the new threshold to view affected payments.
Stripe Radar gives each charge a numerical risk score between 0 and 99, where 0 is the lowest risk and 99 highest.
Block payments
The default blocking threshold is 75, meaning Radar blocks charges with a score of 75 or higher. If you decrease your threshold, you’ll block more payments.
You must enable the default block rule or an equivalent custom rule for Radar to block transactions based on this threshold.
Manual reviews
The default manual review threshold is 65, meaning Radar sends charges with a score of 65 or higher to manual review. Changing the blocking threshold automatically changes the manual review threshold accordingly.
You must enable the default block rule or an equivalent custom rule for Radar to send transactions to manual reviews based on this threshold.
Adjust your threshold
When you change your blocking threshold, you see the following statistics:
| Metric | Description |
|---|---|
| Estimated fraud volume that is blocked or allowed | The estimated volume of fraudulent payments that will be blocked or allowed at the new blocking threshold. |
| Estimated good volume that is blocked or allowed | The estimated volume of good payments that will be blocked or allowed at the new blocking threshold. |
| Estimated previously blocked volume that is blocked or allowed | The estimated volume of previously blocked payments that will be blocked or allowed at the new blocking threshold. Because these payments were blocked and never processed, some of these payments might be fraudulent. |
| Fraud rate by volume | The percent of payments by volume that have received a dispute, an Early Fraud Warning (EFW), or were refunded as fraud. |
| Block rate by volume | The percent of payments by volume that were attempted but were blocked by Radar or by Stripe. Payments are blocked by Stripe to protect you from card testing and other risks that affect all users, regardless of your usage of Radar. |
You can customize the default threshold to fit your own business needs. Setting the risk score threshold requires you to consider a tradeoff between how much fraud Radar blocks and how many payments it allows.
Block more fraud
If your business is experiencing higher rates of fraud, you can decrease the score for blocking payments. To determine what risk score is right for your business, hover over the Block additional payments by setting your acceptable risk score chart.
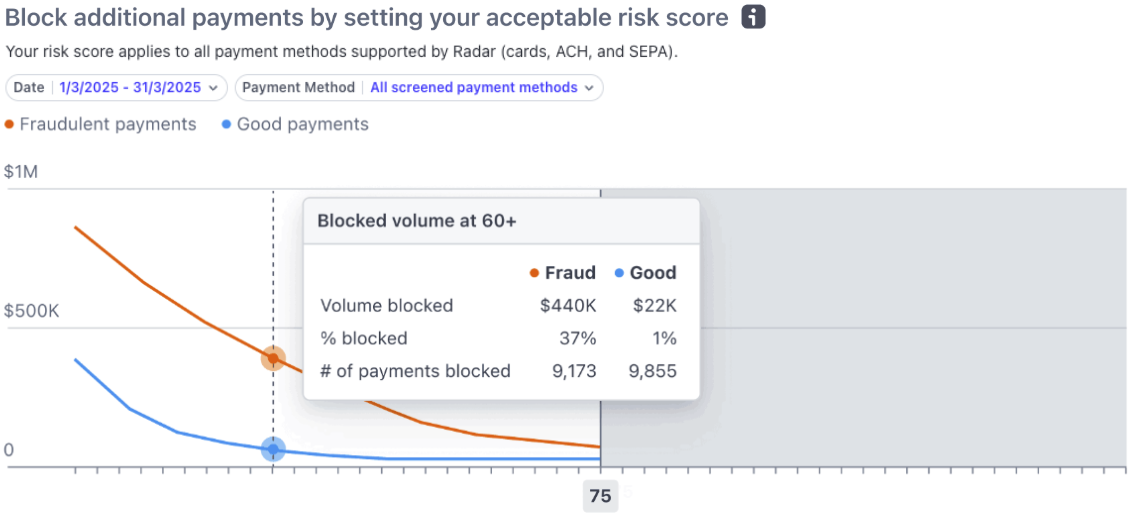
This chart shows how many fraudulent and good payments you would’ve blocked if you set your threshold at that risk score. Here, you can see:
| Metric | Description |
|---|---|
| Volume blocked | Volume of fraudulent and good payments would be blocked. |
| % blocked | The percent of fraudulent and good payments that are blocked respectively. For example, blocking at 65 would result in 55% of your fraud getting blocked at the expense of only 1% of good payments. |
| # of payments blocked | Number of fraudulent and good payments would be blocked. |
Ultimately, you must decide your tradeoff tolerance between how much fraud versus good payments you block.
Allow more payments
If your business has low fraud rates and costs, you might want to increase the default blocking score so that you can allow more payments overall.

This chart shows how many payments you would allow if you set your threshold at that risk score. Here, you can see:
| Metric | Description |
|---|---|
| Volume allowed | Volume of payments would be allowed. |
| # of payments allowed | Number of payments that would be allowed. |
If you’re increasing the risk score for blocking charges, we can’t accurately predict the impact of this change on your fraud rate (as some charges that were previously blocked will now be allowed). Be careful when adjusting the risk score in this direction.
Fraud Controls Private preview
You can find the following controls in the Risk controls section of the Radar Dashboard.
Adaptive 3DS
Radar’s adaptive 3DS control adds an extra layer of authentication during checkout to help you prevent fraud. Stripe’s machine learning runs in the background to authenticate medium-risk payments.
In most cases, 3DS authentication happens with no action required by the customer. If anything looks unusual, the cardholder’s bank might ask the customer to confirm their identity through a security challenge. If 3DS authenticates a payment, the liability for any fraud-related disputes for that payment typically shift from the seller to the issuer. This means that in most cases, the seller isn’t responsible for fraud costs on 3DS-authenticated payments.
Stripe triggers 3DS automatically if required by a regulatory mandate such as Strong Customer Authentication (SCA). Disabling adaptive 3DS doesn’t prevent 3DS from being triggered in cases where it’s required for compliance. Authentication fraud prevention control also isn’t available in testing environments.
Dynamic risk threshold
Note
Dynamic risk threshold applies to card payments only.
Radar’s dynamic risk threshold control automatically adjusts your fraud blocking thresholds according to detected risk. Stripe’s machine learning continuously monitors for fraud trends and temporarily lowers the blocking threshold to a more aggressive level during detected fraud attacks. After the attack subsides, it readjusts back to your default block thresholds.
The control operates transparently in the background. You don’t need to create custom rules or adjust settings during an attack. Dynamic risk threshold honors your manual threshold settings if they’re more aggressive. You can monitor the performance and review affected transactions through detailed analytics in your Dashboard. This automated approach reduces your need to:
- Manually detect fraud patterns
- Create emergency rules
- Remember to adjust settings back after an attack ends
Dynamic risk threshold is available to you if you use Radar for Fraud Teams. You can enable or disable it in the Radar Risk controls section of the Dashboard. You can also view backtesting results showing how it would have performed during past fraud incidents.